Cloud services have burst upon us like a supernova, simultaneously expanding and changing network traffic patterns. The light of a supernova is also a metaphor for freedom. Like clouds floating in the sky, the internet cloud frees users from old restraints. Business users and individuals can access cloud computing and applications on-demand, at any time, from anywhere, for as much as they want and as long as they want, and pay only for what they use. It also frees IT departments from maintaining a physical infrastructure and dealing with software updates and bug fixes. Businesses can focus on managing and customising cloud-based applications for their organisation’s needs.
But freedom also eases open the door to those who would do harm – who would maliciously disrupt corporate operations and steal confidential information. So it is probably no surprise that in a Current Analysis survey of IT users, out of 14 categories, security was the biggest concern by far in moving to a cloud-based strategy. In second place were data privacy concerns.

USS Jimmy Carter was said to have the ability to intercept data carried over optical fibre cables on the ocean floor, probably the most expensive method of wiretapping ever. Here the nuclear submarine is escorted out to sea
At a high level, there are two basic ways that optical suppliers can help businesses deal with these challenges:
- Protecting data in transit – Encryption of the communications channel to protect against interception of data as it is transmitted over a network.
- Protecting data while in the private network – A suite of cyber security applications that examines packets entering a system to see whther they have legitimate business, or if their aim may be system infiltration for the purposes of disruption or stealing data.
Need for multilayer encryption
Encryption has a history going back thousands of years when Greek generals wrote orders along a belt of leather wrapped around a spear of known width. If the belt were intercepted, the letters would appear as garbled nonsense. Since then encoders have devised increasingly sophisticated techniques to encrypt the plain text message, all based at their core on simple letter substitution, and on means of distributing keys between the sending and receiving parties to lock and then unlock the code. A pinnacle of modern encryption is AES-256 (Advanced Encryption Standard with a 256-bit key), which would take thousands of years to crack by brute force, by which time of course the information is useless. To address the trickier problem of key sharing – and it is tricky precisely because the key cannot be encrypted – we rely today on ingenious methods such as Diffie-Hellman key sharing, which uses a combination of private keys that are never transmitted, and public keys that can be known to everyone.
We need such sophisticated techniques because hackers are continuously trying to find and exploit weaknesses in the systems used to implement encryption. Perform an internet search on ‘cryptographic attacks’ and you will find articles containing more than one hundred entries. One popular method is called man-in-the-middle, where an application sits between the sender and receiver and impersonates both, continually forwarding messages back and forth while simultaneously reading them.
As a result, businesses have begun relying on multilayer encryption, as illustrated in Figure 1. If a hacker gains access to even partial information at one level, they can be stymied elsewhere. This uses the same approach as multiple levels of physical security with fences, door locks, alarm systems, and safes.
When internet browser applications want an encrypted session with each other, such as for financial transactions, they use Secure Sockets Layer (SSL) at the application layer (at the top of the OSI protcol stack). You know this is being applied when a little green icon appears in the browser address bar. Another popular place to apply encryption is in routers at the network layer (Layer 3 in the OSI model) using Internet Protocol Security (IPsec).
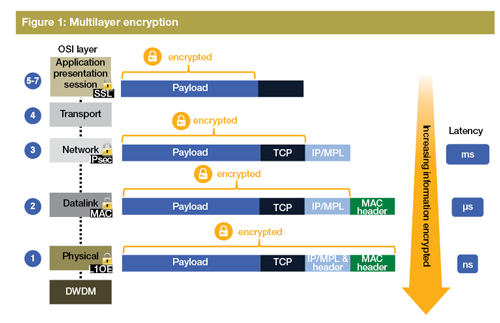
However, encryption at higher layers is not always enough to stop the determined hacker. The shift to cloud computing has transferred attention to the optical fibres that underlie the high-speed communications from businesses to data centres, and between the data centres themselves. These fibres constitute very long unprotected paths and can be tapped at any point using clip-on devices that cost less than $100. The taps divert a tiny, undetectable percentage of the fibre’s light, but still enough to give the hacker access to all the information on the fibre. The hacker can even benefit if a message is encrypted at the application or IP layer, because the address headers at any particular level cannot be encrypted, as these are needed to send a message to its next stop. To a hacker, simply understanding which parties are communicating with each other, and with what frequency and volume, can assist them in breaking into a system in other ways.
The solution is to employ Layer 1 optical encryption (L1OE), which protects all the information on an optical fibre from tapping attacks, including the address headers in higher layers. L1OE can be applied to popular 10G and 100G links used for data centre communication, and it is protocol agnostic; in other words, it is totally indifferent to whatever services are being transported on the fibre, whether Ethernet, Fibre Channel, or InfiniBand. A huge advantage of L1OE is that it operates at wire speed, adding virtually no latency to the transmission. This is increasingly important for supporting emerging edge computing applications that are purposefully deployed closed to the users to minimise delays.
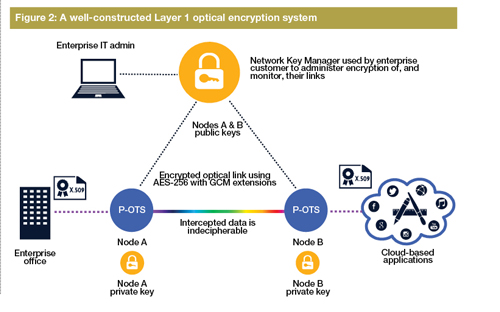
Figure 2 illustrates the key ingredients in a well-constructed L1OE implementation. A network key manager is operated by the enterprise customer or data centre operator and performs two key tasks. It authenticates the identities of the communicating optical nodes using X.509 certificates, and distributes public keys to the nodes to enable them to create a unique session key. This is then used to encrypt the information flowing across the optical link, typically using AES-256. This can be made even more secure by adding GCM (Galois Counter Mode) extensions that ensure no two messages are encrypted in the same way, and can also indicate if a hacker is attempting to tap the fibre.
Principles of cyber security
While encryption protects data from interception, cyber security applications protect against hackers who want to infiltrate or disrupt our systems, often pretending to be a legitimate user. These generally operate at choke points as packets cross from a public to a private domain.
At a basic level, cyber security can be thought of as a passport control officer, and packets as those long lines of people snaking back and forth to enter the country. In the same way that a passport control officer examines the passport and information card you fill out, cyber security examines each and every packet attempting to enter the private domain. Sometimes only the header with address information is examined but, depending on the application and circumstance, it may also inspect the message payload. Cyber security applications can then take various actions, including simply allowing or rejecting entry, or perhaps allowing entry but only after flagging for further investigation because there was something odd and it may be part of a long term infiltration pattern.
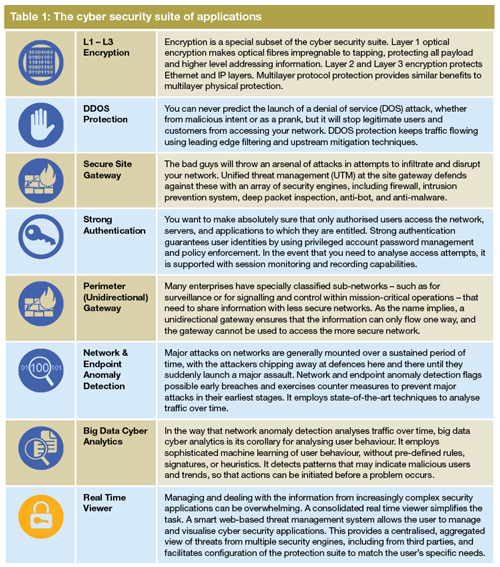
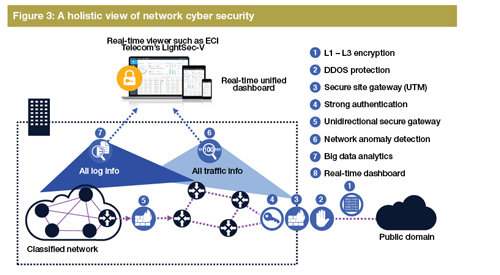
Starting with the cyber security basics, a range of powerful and complementary protection applications can be created. These are depicted in Figure 3 and summarised in the table. Enterprises and data centre operators can pick and choose from among these applications, customising cyber security to suit their business needs.
NFV implementation
Until recently, network customers have been purchasing assorted services, each running on a dedicated appliance connected to the organisation’s network. Operators recognised the complexity and cost consequences of this trend, and the need both to provide faster updates and for new products to reach the market more quickly. So, they asked the European Telecommunications Standards Institute (ETSI) to define the network function virtualisation (NFV) standard to address this issue.
NFV uses commercial computer platforms to implement network services using software, where previously these would have relied on dedicated hardware. This approach has numerous advantages as multiple services can be configured on the same platform, saving money, and it is straightforward to perform software updates for the latest releases or bug fixes.
In this environment, individual cyber security services are configured as virtual network functions (VNFs). The NFV platform can then apply ‘service chaining’, linking a series of appropriate security applications that steer the traffic to the pertinent cyber security VNFs. For example, an email service chain might include virus, spam and phishing protection. Since all of the functions are hosted in the same appliance, this makes the process a lot shorter and simpler, saving considerably on network and application resources.
Physically the NFV platforms can be deployed at various choke points in the network where traffic crosses from public to private domains, as illustrated in Figure 3.
The platforms themselves can be stand-alone modules or blades integrated into the packet transport systems. The NFV-based security services can be delivered by multiple types of service provider or vendor, including by communications service providers as a value-added offering to their business customers, or by data centre operators or cloud content providers as a cloud-based service.
Freedom with peace of mind
Just as society sees a continuous push-pull between maintaining personal freedom and placing restrictions on our freedom to protect ourselves, so it is in the internet cloud. The freedom to innovate also facilitates hackers who would do us harm. Thankfully technology also provides mechanisms to protect ourselves in the form of multilayer encryption and cyber security suites.
Indeed, these capabilities are now being integrated into the telecommunications fabrics connecting business customers to the cloud. Packet-optical transport equipment directly supports features such as Layer 1 optical encryption, and rich cyber security suites can be delivered as virtualised network functions. Optical systems vendors are doing their bit in building peace of mind to support the move to the cloud.
- Jonathan Homa is director, portfolio marketing, at ECI Telecom, www.ecitele.com
- This article is based on a presentation delivered at Next Generation Optical Networks nextgenerationoptical.com

