If you think practical quantum computers arriving within 5-10 years means you don’t need to worry about their impact on communication network security yet, you’re in for a nasty surprise. That’s according to Jane Melia, vice president of strategic business development at Canberra, Australia-headquartered quantum security system vendor QuintessenceLabs. Adopting new security technology takes at least two years, and that protection must often continue for more than five years, so ‘this deadline is actually very close indeed’, she warns.
 Quantum computers will challenge existing communication privacy signature schemes where the key used to encrypt and decrypt messages depends on difficult computations. One of the most popular, the RSA algorithm, uses a large number as a public key, obtained by multiplying two prime numbers, which are kept private. Eavesdroppers trying to decrypt the message by working out the prime numbers will be able to do so exponentially faster using quantum computer algorithms than with conventional computers. ‘This problem, which would take around 3000 years to solve using classical computers for a 1024 bit key, could now be solved in a matter of minutes,’ Melia said.
Quantum computers will challenge existing communication privacy signature schemes where the key used to encrypt and decrypt messages depends on difficult computations. One of the most popular, the RSA algorithm, uses a large number as a public key, obtained by multiplying two prime numbers, which are kept private. Eavesdroppers trying to decrypt the message by working out the prime numbers will be able to do so exponentially faster using quantum computer algorithms than with conventional computers. ‘This problem, which would take around 3000 years to solve using classical computers for a 1024 bit key, could now be solved in a matter of minutes,’ Melia said.
Yet, quantum phenomena also offer a solution. Rather than a public key system, where privacy is ensured by computational difficulty, light can be used to generate a private key known only by the sender and recipient. The resulting, truly random key becomes a ‘one-time pad’, the only existing mathematically unbreakable encryption – which QuintessenceLabs is developing systems to deliver. Switzerland’s ID Quantique, and Japanese giants Toshiba and NTT are among the other companies developing or actively producing such quantum key distribution (QKD) systems. Yet they see varying interest from those who should be preparing for the quantum computing challenge.
Random success
As a stepping stone towards QKD, QuintessenceLabs is making existing cryptographic approaches safer by offering true random number generators that use quantum phenomena to replace existing pseudorandom number generators. In RSA encryption, for example, pseudorandom number generator algorithms usually pick the prime numbers, opening the door for weaknesses, Melia explains. ‘These types of random numbers have caused breaches,’ she said. ‘Generating true random numbers is actually a really hard problem that we have struggled to solve while delivering commercial throughputs and at acceptable costs.’
Melia’s company splits a laser beam in two and detects the differences between the resulting beams in its qStream random number generators. ‘By carefully measuring and then digitally processing quantum fluctuations, we generate ultra-high bandwidth random numbers,’ Melia said. ‘The current generation is about the size of a cell phone and sits on a standard PCIe card. Our next-generation product will be released at the end of 2016, and will be half that size for the same performance.’
qStream delivers 1Gb/s of completely random bits, most often deployed as part of a key management system. It is integrated into QuintessenceLabs’ Trusted Security Foundation product, which is currently deployed at the Australian bank Westpac, and the global data centres of a leading cloud storage provider. ‘Pilot projects are also underway with a number of defence prime contractors and government agencies,’ says Melia.
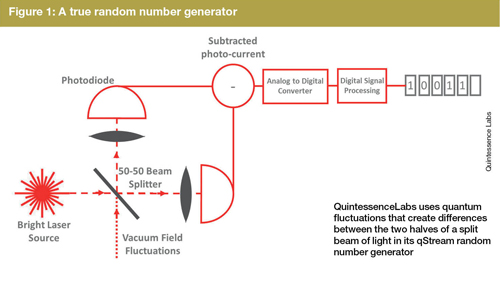
But, as well as helping today’s security, a raw stream of truly random bits will help form the encryption keys in QKD. In this system a sender, Alice, can encode a long random sequence of 0s and 1s onto 1550nm photons and send them to a recipient, Bob, over an optical fibre. In the first ever QKD protocol proposed, called BB84, Alice chooses between two methods for assigning 0 or 1 values to photons. She can either use circular polarisation, with right-hand or left-hand polarisation indicating the two values, or linear polarisation, where the values are represented by horizontal or vertical polarisation. Bob chooses to measure either circular or linear polarisation, obtaining the correct result only if he has chosen the same basis as Alice. Approaches like this that depend on the particle nature of light are known as discrete variable QKD (DV-QKD).
‘Alice and Bob have suddenly got a string of random bits, and from this you can make a key for cryptographic applications,’ explains ID Quantique’s Bruno Huttner. And, unlike classical optical communication, where information can be stolen from the physical layer by splitting light out, nobody can know what this key is, Huttner underlines. That’s because quantum information encoded on a single photon cannot be split. The only choices are to take it all or leave it all, meaning stolen data completely disappears. Alice and Bob will know there’s an eavesdropper if the error rate gets too high.
Rather than the asymmetric RSA algorithm, QKD systems therefore use symmetric encryption schemes, with ID Quantique’s Cerberis systems employing the Advanced Encryption Standard with a 256-bit key (AES-256). ID Quantique’s initial instruments used photon polarisation, but the company found this property hard to control in optical fibres, Huttner reveals.
Coherent story
ID Quantique now uses a protocol devised in collaboration with the University of Geneva called coherent one-way (COW). In COW, Alice sends attenuated coherent laser pulses containing either no photons or that probably have one photon, with very low probability of having more than one. 0 is encoded by a photon-containing pulse followed by an empty pulse, and 1 is encoded by an empty pulse followed by a photon-containing pulse. Interspersed among these are decoy pulses with two consecutive photon-containing pulses. Bob can use the decoy pulses to measure coherence, from which he can determine an error rate. Separately, Alice can tell Bob which parts of the bit string to use as a key without needing to hear back from Bob.
‘You only need an active optical transmission component on Alice’s side, which makes the whole system easier to implement,’ Huttner explained. ‘From the error rate you derive the maximum amount of information that could have leaked to an eavesdropper. Then you use “privacy amplification”, which allows you to reduce this information down to about zero.’ ID Quantique has not yet discovered any eavesdroppers in the real world, he adds. ‘In our deployments, sometimes the number of errors would increase dramatically for a few seconds. In a few cases this was just a nearby train making vibrations, which were seen as errors.’
Toshiba similarly uses attenuated lasers in its approach, the T12 protocol, based on DV-QKD. Marco Lucamarini, senior research scientist at Toshiba Research Europe Ltd in Cambridge, UK, emphasises that attenuated lasers are cheaper than single photon sources. They are also more efficient for QKD as they emit more pulses per second. T12, like BB84, has two options for encoding 0s and 1s, both involving shifting the phase difference between two coherent light pulses. One option records 0 when the phase is shifted 0° and 1 when it is shifted 180°, and the other counts 0 at 90° and 1 at 270°.
The T12 protocol also modulates intensity, with Alice randomly choosing between three possible average photon numbers. The intensity where 40 per cent of the optical pulses contain photons is the true signal, and intensities where only 4 per cent or 0.1 per cent of pulses contain photons are decoy signals. As in COW, the decoy signals help the recipient estimate the fraction of photons actually detected on the receiver’s side. ‘In the T12 protocol, these two parts are optimised to guarantee the highest possible key rate,’ Lucamarini says.
NTT Basic Research Laboratories in Kanagawa, Japan, has developed two DV-QKD protocols where Alice again exploits phase shifts to send a bit sequence, explains senior research scientist Hiroki Takesue. ‘In differential phase-shift QKD, we measure only the phase difference between adjacent pulses in a continuous pulse train,’ Takesue explained. ‘In round-robin DPS-QKD, we implement a measurement setup by which we can measure the phase differences of any two pulses at random from a packet containing many pulses.’ The former is much easier to implement than the latter, but is less secure, he adds, although for attacks that are likely in the real world, both protocols are very safe.
Going the distance
In addition to QKD protocol complexity, a significant implementation challenge comes when sending the very weak QKD signals down optical fibres, which can absorb the individual photons. ‘The photons initially prepared and sent in the channel are attenuated during propagation and only a small proportion reaches the receiving side,’ Lucamarini said. ‘For a standard singlemode fibre in the third telecom window, the attenuation coefficient is 0.2dB/km, meaning only 50 per cent of the initial photons survive after 15km, only 25 per cent after 30km, and so on.’
Consequently, often only single-photon detectors are sensitive enough for such applications, and even they have limitations, Takesue comments. ‘When the number of received photons is overwhelmed by the detector noise, we cannot send the key anymore,’ he said. ‘Thus the transmission fibre loss limits key distribution distance, typically to 100km.’ Increasing the key distribution distance is important to increase the market QKD can serve’, he adds. China is attempting just this with a 2,000km-long quantum backbone between Beijing and Shanghai, due to be operational by the end of 2016.
‘On the other hand,’ adds Lucamarini, ‘I personally believe that QKD became more appealing to investors when it was demonstrated to co-exist with 10G and 100G metropolitan networks over distances of about 100km.’ That’s comparable to the diameter of the world’s busiest cities, he emphasises. ‘If it is true that of the 7 billion people in the world, 4 billion live in cities, then QKD is already suitable to serve more than 50 per cent of the global population.’ The experiment to which he refers was published in 2012, when Toshiba Research Europe demonstrated that quantum key distribution is feasible over metropolitan area networks carrying live data traffic. It used wavelength multiplexing to combine QKD with classical signals on the same fibre. In 2014, Toshiba achieved stable communication of quantum keys for 34 days over standard optical fibre.
The current working solution for longer-distance QKD is based on “trusted nodes”, the Toshiba scientist adds. ‘The overall distance between two endpoints in a network is split into a number of sub-links, each connecting two nodes,’ Lucamarini says. ‘If the endpoints of each sub-link are owned by a trusted authority, the overall communication is guaranteed to be secure. Sometimes you don’t want to have “trusted authorities” around. In this case, if the network is large enough, it is possible to split the initial secret into several parts and then send each part through a different route in the network. Only the endpoints – Alice and Bob – will receive all the parts necessary to reconstruct the initial secret, whereas the intermediate nodes will have only access to a meaningless part of it. This way, the trust in third parties can be partially removed.’
At each trusted node, one key is received and a new one transmitted, Huttner explains. ‘Then you do some processing to make an overall key that works from one side to the other,’ he says. ‘It’s called a trusted node because the node knows everything. That could be one reason why China is keen on QKD – the government is responsible for the nodes, and has access to all the secret information.’ The Chinese project also has short distances between nodes to increase transmission rates, notes Huttner. ‘But of course you need more links, which means you need more systems, and that is more expensive.’
Yet the 100km range of ID Quantique’s Cerberis QKD system has been enough for commercial deployments. For example, it has enabled Geneva-based companies and financial institutions to securely transfer information to a remote disaster recovery data centre 70km away. The Geneva government has also used Cerberis in every federal and cantonal election and local internet referendum since 2007. This application also exploits the company’s true random number generator, Quantis, which, like QuintessenceLabs’ qStream, exploits quantum fluctuations, but using a slightly different optical setup. Quantis produces unique personal identification numbers for each citizen, and then generates encryption keys for each internet voting session.
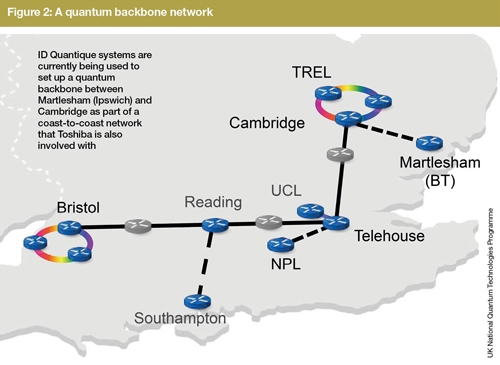
However, ID Quantique’s collaborators at the University of Geneva have achieved QKD over 300km experimentally. In collaboration with the UK Quantum Communications Hub, a government-funded industry-academic partnership for quantum technologies research, the company is also building a quantum backbone that will stretch from BT Adastral Park in Ipswich, across to the University of Bristol on the opposite coast (see figure 2). The Hub ‘has purchased quite a few systems from us’ for the first leg, from Ipswich to the University of Cambridge, according to Huttner. ‘BT is very interested in QKD,’ he adds.
Commercial uncertainty
Toshiba Research Europe is also involved in the UK Quantum Communications Hub, but Toshiba’s QKD systems are already in use in Japan. ‘The T12 protocol shows exceptional performance and adaptability to different environments,’ Lucamarini said. ‘The Genome system in Sendai is an example of that.’ QKD is used to encrypt real data between the Toshiba Life Science Analysis centre and the Tohoku Medical Megabank. ‘Genome data is one of the best examples of information requiring long-term protection. A genetic problem can travel across generations and the people affected by it have the right to keep the secret. Everlasting protection of confidential data is what QKD can do best.’
Meanwhile, NTT’s DPS-QKD system is now being operated in a testbed quantum backbone in Tokyo, although Takesue has seen few opportunities elsewhere. ‘In our company, we simply cannot find any market yet,’ he said. ‘Currently QKD has lots of limitations. The maximum distribution distance is only 100km, the key rate is low, and it is very expensive. We need to overcome such drawbacks to find customers.’
Quintessence Labs’ Melia likewise sees a growing number of pilot projects and a steeply increasing research and development effort, but relatively slow commercial adoption. Her company’s QKD activities have been focussed in Australia, including a demonstration in production fibre-optic networks from 2010 to 2014. ‘In the subsequent two years, the working prototype has been modified to improve its reliability and security,’ she explained.
There’s growing interest in moving from DV-QKD to continuous variable QKD (CV-QKD), Melia says, which exploits light’s wave nature to achieve secure key distribution. ‘Information is encoded onto the amplitude and phase quadratures of a coherent laser by the transmitter,’ she said. Although CV-QKD is a much younger technology, it promises superior cost, form factor, power consumption, and performance, Melia claims. On the downside, CV-QKD brings other problems, including ensuring security at long distances, and the return of the spectre of eavesdropping by splitting out photons.
Overall, uptake is slow because organisations do not necessarily have the budget, time and expertise to address today’s cyber-security breaches, let alone to think about the future, Melia says. ‘There is a parallel lack of awareness of solutions available to address the problem,’ she added. ‘On the other hand, it is true that solutions and the QKD industry as a whole do still need to mature and become truly commercially ready. Many companies will be reluctant to take the risk of being the first adopters.’
Nevertheless, Melia feels that QKD will take off soon. ‘Waiting until quantum computers are a practical reality will really be too late,’ she stressed. ‘The public key infrastructure that we use to secure the exchange of keys, and with that international trade, for example, will be broken. But there is an increasing effort in communicating on this issue. I expect that awareness will continue to grow, and in parallel for solutions to mature over the coming years so that we are in a position to address this.’
● Andy Extance is a freelance science writer based in Exeter, UK


